Tool masquerades as ransomware but overwrites and destroys data making it unrecoverable, Kaspersky warns
Security researchers at Kaspersky have spotted a new disk wiping malware tool dubbed CryWiper landing on target systems, disguised as ransomware.
So far, researchers at the security vendor have only observed the operator of the malware deploy CryWiper in “pinpoint attacks” on targets in Russia. But that’s no guarantee that the attackers won’t soon deploy it against other targets.
CryWiper is malware that hunts for and corrupts files that are not essential to the functioning of the operating system, according to Kaspersky. For instance, it directly overwrites documents, databases and archives on an infected system while ignoring files with extensions such as.exe, .dll, ,lnk and, .sys. CryWiper also gives a pass to several critical folders in the C:\\Windows directory.
“At the first glance, this malware looks like ransomware,” said Kaspersky in a blog Friday. “It modifies files, adds a .CRY extension to them (unique to CryWiper), and saves a README.txt file with a ransom note, which contains the bitcoin wallet address, the contact e-mail address of the malware creators, and the infection ID.”
However, victims that might be inclined to pay a ransom to get their data back would do well not to do so. That’s because any file that CryWiper modifies is un-restorable to its original state, Kasperky said. “So if you see a ransom note and your files have a new .CRY extension, don’t hurry to pay the ransom: it’s pointless.”
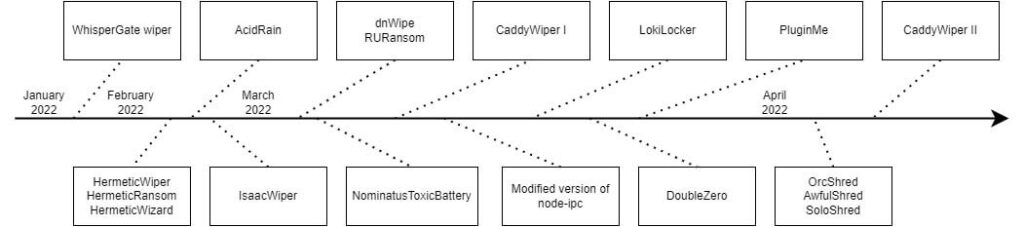
Source: Trellix
The 2022 wipermania
CryWiper is one of several disk-wiping malware tools that have surfaced this year and present a threat to enterprise organizations. A study, that a researcher at Trellix presented at Black Hat Middle East & Africa last month, identified the war in Ukraine as driving a surge in wiper attacks in 2022. Examples of wipers that threat actors—most of them Russia based, or Russian-government sponsored—have used in attacks on Ukrainian government and private organizations include HermeticWiper, WhisperGate, CaddyWiper and IssacWiper. Often these tools have masqueraded as ransomware and included messaging designed to lure users into believing they could get their data back by paying a ransom.
Unlike ransomware operators, who are typically financially motivated, threat actors deploying wiper malware tend to be hacktivists or those working to support the goals of a larger sponsor—such as a nation state. Their attacks are almost always destructive and disruptive. That appears to be the case with CryWiper as well. Kaspersky said its analysis showed the creators of the have deliberately craft it to wreak havoc. “Our experts are confident that the main goal of the attackers is not financial gain, but destroying data,” the security vendor warned.