Image source: MITRE Caldera
Users should patch immediately to mitigate risk, Caldera security team says.
MITRE’s Caldera team has patched a maximum severity remote code execution bug in the adversary emulation platform and wants all users to immediately pull down the latest—and recently fixed—version of the software.
Maximum Severity Threat
The bug, CVE-2025-27364, affects all versions of MITRE Caldera including the earliest releases and gives attackers a way to gain trusted and highly privileged access to Caldera environments, from where they can launch potentially devastating attacks.
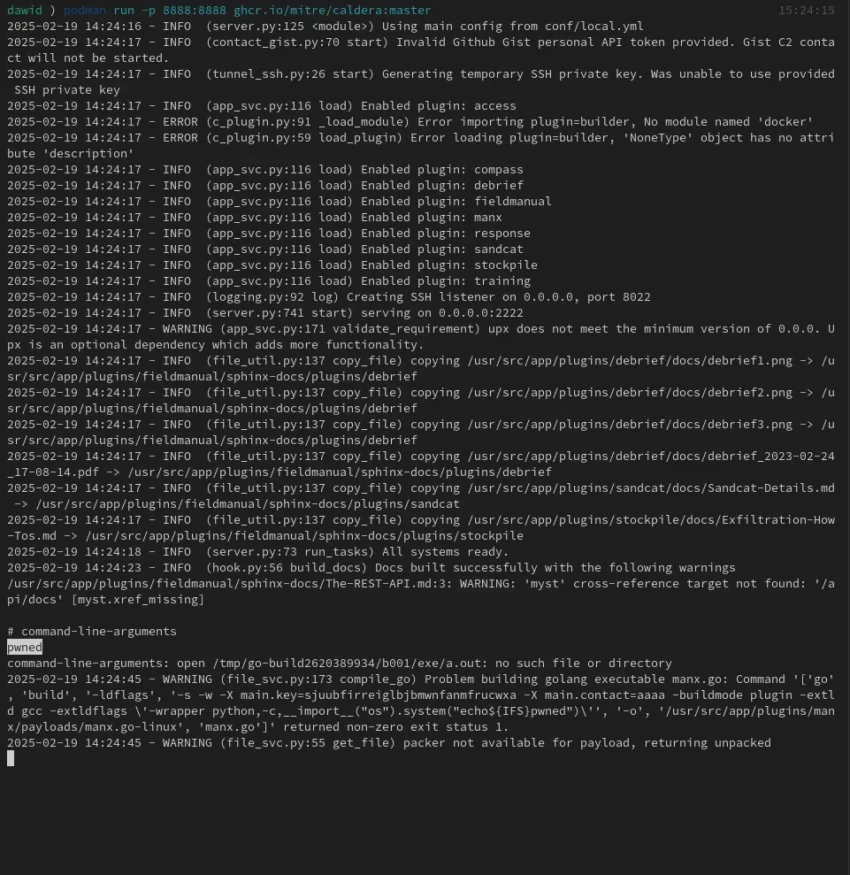
Independent security researcher Dawid Kulikowski discovered and recently reported the bug to the MITRE Caldera team. In a post on Medium, Kulikowski identified the vulnerability as easy to trigger under default configurations and not requiring any additional privileges or special setup. The only prerequisites for exploitation, according to Kulikowski, are the presence of Go, Python, and GCC on the system hosting the Caldera server, all of which are common dependencies for many environments using the framework.
Key Takeway: MITRE Caldera is an automated open-source adversary emulation framework that many organizations use for testing network defenses and conducting red team exercises. Vulnerabilities in products like MITRE Caldera are especially concerning because they transform trusted security testing tools—which often run with elevated privileges and exceptions from defensive controls—into potential attack vectors that can be exploited to compromise the very systems they were designed to protect. Kulikowski has developed a proof-of-concept exploit for CVE-2025-27364 but posted only a slightly modified version of it on Medium to make it harder for script kiddies to leverage it. He however plans to release a full-fledged Metasploit module for it in a few weeks which means users best patch before then.
CVE-2025-27354 has to do with a dynamic compilation functionality of Caldera’s Manx and Sandcat agents. A lack of proper authentication during the compilation process basically gives attackers an opening to inject malicious code and take over an organization’s Caldera server. Since the Caldera agents are designed to execute commands dynamically as part of normal operations, this vulnerability effectively provides a direct pathway for attackers to gain control over the server and any connected assets. One big concern is the potential for attackers to hijack ongoing security tests and turn simulated attacks into actual malicious attacks without immediately raising suspicion.
Generally, the types of vulnerabilities that would be particularly concerning in a tool like Caldera include authentication bypass vulnerabilities, command injection in the agent control mechanisms, privilege escalation within the platform and insecure handling of operational data.