Sansec says it has observed more probes in November against the now-patched zero-day flaw (CVE-2022-24086) than the rest of the year combined.
Seven threat groups affiliated with the Magecart cybercrime syndicate have begun heavily targeting a critical, arbitrary code execution vulnerability in the Magento 2 and Adobe Commerce platform that powers tens of thousands of e-commerce stores worldwide.
The vulnerability (CVE-2022-24086), that Adobe patched in February 2022, affects Adobe Commerce versions 2.4.3-p1 and earlier and versions 2.3.7-p2 and earlier. It stems from the software’s failure to validate user input during the checkout process. Attackers can use the flaw to compromise Magento 2 and Adobe Commerce powered e-commerce sites and deploy persistent remote access trojans, backdoors and other malware on them. Exploiting the flaw requires no user interaction.
CISA included the Magento and Adobe Commerce vulnerability in its Known Exploited Vulnerabilities catalog in February. Federal executive civilian branch agencies had until March 1 to address the vulnerability.
Sharp increase in Magento attack activity
In an Nov 15 advisory security vendor Sansec said it had observed a sharp increase in Magecart scans targeting the vulnerability over the last several weeks. The number of scans in November in fact appears well on track to beat the total number of attack probes in the past nine months combined, Sansec said. The security vendor attributed most of the malicious activity to seven groups affiliated with Magecart, a long running criminal syndicate comprised of dozens of smaller groups engaged in online credit card theft and fraud. “(The trend) paints a grim picture for ecommerce DevOps teams worldwide for the coming weeks,” Sansec said.
Sansec described the Magecart attack scans as involving attempts by the threat actors to place, “TrojanOrders” or fake orders at target websites in a manner that triggers an automated response containing code for exploiting the vulnerability, from the target website.
“A probe means trying to trigger the system to send an email, with the exploit code in one of the fields.” Sansec said. “An email is, among others, triggered by placing an order; that is why we call this attack TrojanOrder. Other triggers are “sign up as customer” or “share a wishlist.” A successful probe means the attacker can take over the website.”
Sansec said it had observed threat actors exploiting the Magento and Adobe Commerce vulnerability to immediately install a remote access trojan on the compromised e-commerce site to ensure easy and permanent access to it even after a site owner might have patched the vulnerability. “In the attacks we investigated, this backdoor is often, but not always, hidden in the file health_check.php, normally a legitimate Magento component,” Sansec said.
Large number of Magento, Adobe Commerce sites remain unpatched against the flaw
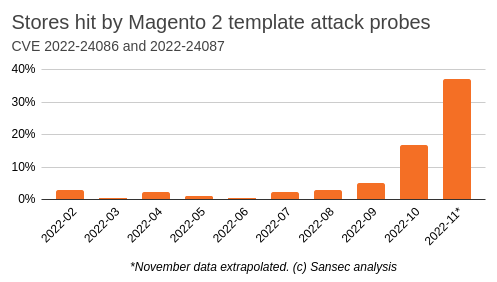
In a previous blog post in September Sansec had reported all attacks it had observed as being interactive likely because the Magento checkout flow is very hard to automate. “It starts with the creation of a new customer account and an order placement, which may result in a failed payment. The sales_order_address table now contains a record with malicious template code,” for installing the RAT. Sansec estimated that Magecart actors have hit a staggering 38% of all Magento and Adobe Commerce websites with these TrojanOrders just in November.
CVE-2022-24086 was one of two critical vulnerabilities that Adobe disclosed (and patched) in Adobe Commerce and Magento Open Source in February. The other one is CVE-2022-24087, another critical remote code execution vulnerability that Adobe discovered while developing a fix for the first one.
Adobe issued updates addressing both flaws in February 2022 and urged organizations using the affected software to immediately update to the new versions, However, according to Sansec, nine months later, about one-third of Magento and Adobe Commerce sites remain unpatched against the vulnerabilities despite the fact that threat actors were actively exploiting CVE-2022-24086 even before a patch for it became available.