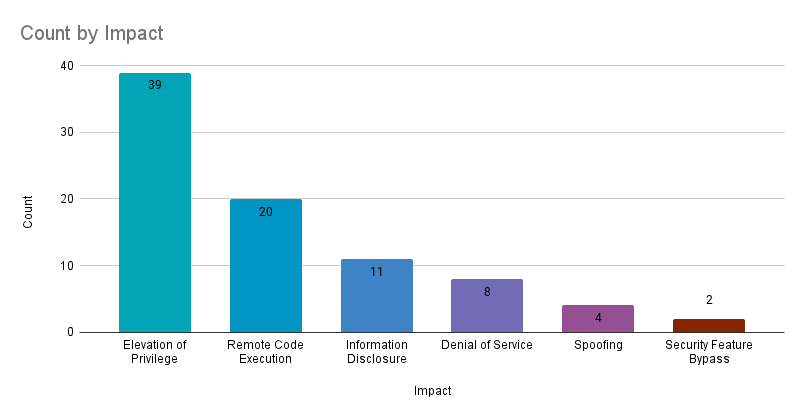
Microsoft released fixes for a total of 84 CVEs across its products [300 words].
One of the vulnerabilities that Microsoft patched today is a zero-day that is being actively exploited: Windows COM+ Event System Service Elevation of Privilege Vulnerability (CVE-2022-41033): An attacker could gain system level privileges.
Two other recently disclosed zero-days (CVE-2022-41040 and CVE-2022-41082) remain unpatched.
13 of the vulnerabilities in the Oct. 2022 update were rated Critical
- Microsoft SharePoint Server Remote Code Execution Vulnerability (CVE-2022-41038): An authenticated attacker with Manage List permissions could execute code remotely on the SharePoint Server. Exploitation more likely.
- Windows CryptoAPI Spoofing Vulnerability (CVE-2022-34689): Enables an attacker to spoof the identity associated with an existing public x.509 certificate. Exploitation more likely
- Azure Arc-enabled Kubernetes cluster Connect Elevation of Privilege Vulnerability (CVE-2022-37968): Vulnerability could allow an unauthenticated use to elevate privileges and gain admin control over Kubernetes cluster.
- Active Directory Certificate Services elevation of privilege vulnerability (CVE-2022-37976): Gives attackers a way to gain domain admin privileges.
- Microsoft Office RCE Vulnerability (CVE-2022-38048): Enables attackers to execute arbitrary code on vulnerable systems.
- Windows Hyper-V Elevation of Privilege Vulnerability (CVE-2022-37979): An attacker in a Nested Hyper-V environment could gain Level 1 Hyper-V Windows Root OS privileges.
The remaining are all Windows Point-to-Point Tunneling Protocol RCE vulnerabilities. All of them allow an attacker to execute arbitrary code on a PPTP server via specially crafted PPTP packets.
- Windows Point-to-Point Tunneling Protocol RCE Vulnerability (CVE-2022-33634)
- Windows Point-to-Point Tunneling Protocol RCE Vulnerability (CVE-2022-22035)
- Windows Point-to-Point Tunneling Protocol RCE Vulnerability (CVE-2022-24504)
- Windows Point-to-Point Tunneling Protocol RCE Vulnerability (CVE-2022-38047)
- Windows Point-to-Point Tunneling Protocol RCE Vulnerability (CVE-2022-41081)
- Windows Point-to-Point Tunneling Protocol RCE Vulnerability (CVE-2022-30198)
- Windows Point-to-Point Tunneling Protocol RCE Vulnerability (CVE-2022-38000)
71 vulnerabilities were of “Important” severity.
Further Reading: