Key takeaway: Don’t allow vSphere Installation Bundles (VIBs) to become a vehicle for sneaking malware into your environment. (276 words)
What happened: A China-based threat actor installed multiple backdoors on ESXi hypervisors at several organizations using malicious vSphere Installation Bundles. The backdoors enable a lot of bad things including persistent access, arbitrary command execution and tampering with logging services.
Why it matters: 1) A VIB is the basic building block of an ESXi image. Administrators use them to manage systems, deploy updates, create startup tasks and other functions. The attacks show VIB are a great vehicle for sneaking malware into an ESXi environment when secure practices are not followed. 2) Workloads and data in VMware environments are often mission critical meaning a breach here could have significant, company-wide implications.
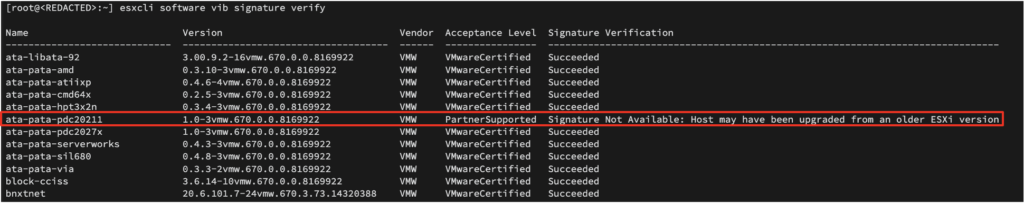
How it happened: VMware recommends that organizations only use secure, signed VIBs that either the company or trusted partners have developed. But sometimes organizations use their own VIBs, or community developed VIBs, to build ESXi images. Here, the attackers developed their own VIBs, dressed them up as trusted, signed VIBs and found a way to install them in targeted ESXi hypervisors using a parameter that VMware has recommended should be disabled.
Measures that might have stymied the attackers according to VMware: Strong authentication and authorization; the use of Secure Boot, Trusted Platform Modules, and Host Attestation to validate software and drivers; blocking use of community developed VIBs; workload hardening and patch management.
The details
Mandiant’s blog on how the attacks happened.
VMware’s advice on how to detect and protectMandiant’s recommended measures for EXSi hardening