Image source: Shutterstock
Enterprise organizations, ISPs and security services providers are not adequately prepared to protect against attacks that leverage the technique, authoring agencies say.
The NSA, CISA, and international partners have issued a rare joint advisory warning organizations about the ongoing threat posed by attack technique known as fast flux. The authoring agencies which include the Australian Signals Directorate, and the Canadian Centre for Cyber Security described fast flux as posing a significant threat to national security because of how the technique enables malicious actors to consistently evade detection.
Here’s what the authoring agencies want you to know
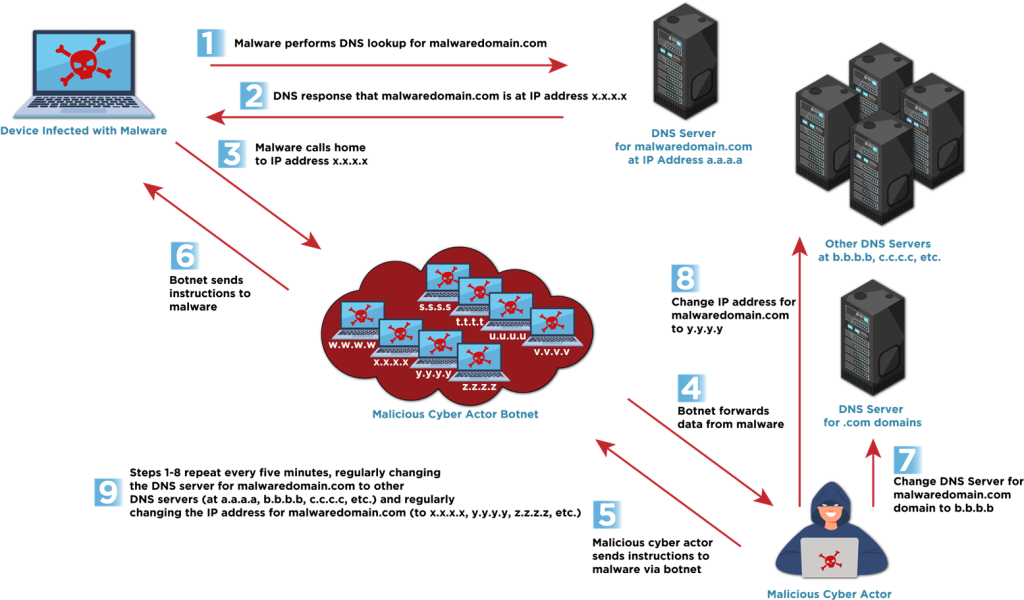
Fast flux is a technique that uses rapidly changing DNS records to make malicious servers harder to track and shut down. It involves constantly updating the IP addresses linked to a single domain, allowing attackers to maintain access even if some IPs are blocked.
There are two main types of fast flux:
Single flux, where a domain is tied to multiple IP addresses that are frequently rotated. If one IP is blocked, traffic is simply rerouted to another.
Double flux which extends this by also constantly rotating the DNS name servers that resolve the domain. This adds another layer of redundancy and anonymity by frequently changing both Name Server (NS) and Canonical Name (CNAME) records. Attackers often use botnets—networks of compromised devices—as proxies in this setup, creating a constantly shifting and hard-to-detect infrastructure.
Quick Take
Who and What: The US National Security Agency, CISA, FBI and international partners in Canada, Australia and New Zealand want enterprise organizations, Internet service providers and cybersecurity service providers to implement protections against attacks that employ fast flux techniques.
Why: Fast flux is a technique to conceal command and control infrastructure and malicious servers and websites through rapid changes to Domain Name System (DNS) records. The technique presents a significant security risk because it enables attackers to evade detection, maintain anonymity, and sustain malicious operations—including phishing, ransomware, and botnet activities—against takedown efforts. Many organizations don’t have mechanisms to affectively address the threat
Where: The threat impacts organizations, Internet service providers (ISPs), and cybersecurity service providers worldwide, with notable instances involving groups like the Russia-backed Gamaredon and ransomware campaigns such as Hive and Nefilim.
How bad actors are using fast flux
Malicious actors, including cybercriminals, nation-state groups like the Russia-backed Gamaredon, and operators of ransomware such as Hive and Nefilim, extensively utilize fast flux to enhance their campaigns. A common use of fast flux is to create resilient command and control infrastructure. The technique enables attackers to maintain operations even in the face of coordinated takedown attempts. Attackers also use fast flux to keep phishing websites up and to make cybercriminal forums and marketplaces more resistant to law enforcement action.
Bulletproof hosting providers further exacerbate the issue by offering fast flux as a service, often advertising features like dummy server interfaces that absorb abuse reports, thereby shielding the true malicious servers from blocklists such as Spamhaus, the authoring agencies said. These providers also employ separate IP pools and globally dispersed domain registrations to enhance reliability for their clients’ illicit activities.
Here’s why it matters
For enterprise organizations and security teams, particularly those in critical infrastructure and defense sectors, fast flux poses a substantial risk. Fast-flux renders IP-based blocking ineffective—due to the rapid rotation of IP addresses. It allows attackers to maintain prolonged access within networks, often for data exfiltration, phishing, or botnet expansion. The anonymity provided by fast flux complicates attribution, hindering efforts to trace malicious activity back to its source. This resilience and obfuscation can strain security resources meaning security teams must continuously adapt to a moving target. The technique’s use in high-profile attacks underscores its potential to enable significant breaches, making it a priority for organizations aiming to safeguard sensitive operations.
Here’s what to do
To mitigate the fast flux threat, the advisory recommends a multi-layered defense strategy.
Organizations should integrate threat intelligence feeds to identify, and block known fast flux domains and IP addresses at firewalls, DNS resolvers, or SIEM systems.
Implement anomaly detection to monitor DNS query logs for indicators such as high IP diversity, low time-to-live (TTL) values—often as short as 3 to 5 minutes—or inconsistent geolocation data. Use network flow analysis to help detect large-scale, short-duration communications indicative of fast flux activity.
Enterprises using Protective DNS (PDNS) services should not assume coverage against fast-flux attacks. Instead, verify that the provider offers services for actively detecting and blocking fast flux activity.
The NSA, CISA and the other authoring agencies also encouraged organizations to share indicators of fast flux attacks through platforms like CISA’s Automated Indicator Sharing and Australia’s Cyber Threat Intelligence Sharing Platform.
